
Challenges and Solutions in Adopting Zero Standing Privileges
Zero Standing Privileges (ZSP) is a leading cybersecurity practice that aims to prevent unauthorized users from gaining access or having their privileges escalated. “Ransomware attacks
Whiteswan revolutionizes cybersecurity by unifying identity management and security controls in one powerful platform. Protecting your digital assets with advanced Zero Trust principles, securing your apps and infrastructure through passwordless access, just-in-time privileges and advanced identity threat detection.












Eliminate permission bottlenecks and human error with Whiteswan’s automated, time-bound access flows. Ensure complete visibility and compliance through granular permissions and detailed audit logs.
Streamline access management and eliminate manual intervention with automated, real-time controls.
Limit access to key infrastructure and data with precise, time-bound permissions, reducing exposure to risk.
Gain 360-degree visibility across all access events, empowering IT teams to monitor and respond quickly.
Secure users and devices with dynamic, identity-centric boundaries to prevent unauthorized access.
Enforce least-privilege principles with fine-tuned permissions, ensuring compliance and minimizing risks.
Neutralize threats instantly with advanced analytics, stopping suspicious activities before they escalate.

Our unified platform delivers unparalleled protection against today’s complex threats. Consolidating the most critical security capabilities, making it easier to manage, scale and adapt. From endpoint protection to secure remote access, we ensure your entire infrastructure is safeguarded.
Whiteswan consolidates identity management, access control, and real-time threat detection into one streamlined platform, making security effortless.
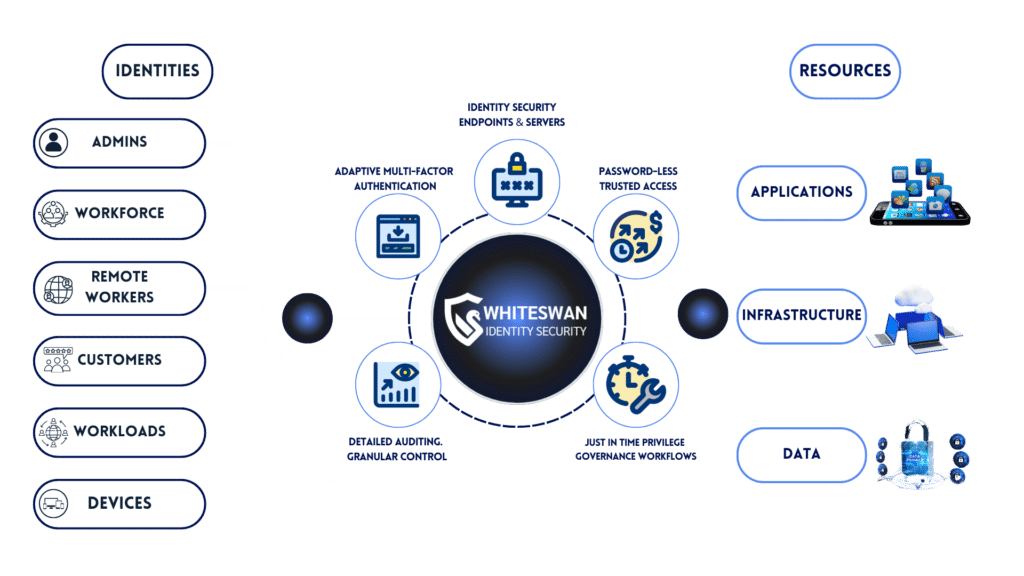

Whiteswan’s platform integrates effortlessly with your existing IT infrastructure, providing robust protection for on-premises, cloud, and hybrid environments.
Whiteswan’s platform streamlines your security operations, making it easier to manage, scale, and adapt your defenses in today’s dynamic threat landscape.


Whiteswan’s identity-first security solutions address unique challenges across various sectors:
At Whiteswan, we’re committed to staying at the forefront of identity security. By choosing Whiteswan’s Proactive Identity Protection, you’re not just securing your present – you’re future-proofing your identity security for years to come. Our ongoing research and development focus on:

With operations spread across multiple industrial sites and a growing network of employees, contractors, and vendors, Rockman faced the challenge of maintaining secure and efficient access to its critical IT infrastructure.
Whiteswan helped us eliminate VPN dependency with a secure, time-bound, and approval-based model, giving complete visibility into both vendor and internal activities through real-time monitoring and session recording.

Incharge – Network & Systems, Rockman Industries Ltd.
Experience the power of innovation with our products. Tailored to meet your specific needs, our solutions are designed to propel your business forward.
Whiteswan Identity Security has greatly enhanced our security and streamlined operations. Their precise identity management reduces risks and protects sensitive data. We value their commitment and look forward to ongoing collaboration.

Manager IT, MG Contractors
Don’t find your answer here? Check out more FAQs on the contact page or just send us a message for any query.
Whiteswan offers a unified Zero Standing Privileges (ZSP) platform, integrating passwordless access, just-in-time privileges, and advanced threat detection to secure your apps and infrastructure.
Whiteswan provides identity-centric security, creating micro-perimeters around users to prevent unauthorized access and lateral movement.
Whiteswan’s ZSP platform offers quick deployment with no complex setup, enabling rapid protection for endpoints, servers, and cloud resources.
Our platform serves industries like finance, healthcare, manufacturing, technology, and government, securing sensitive data and infrastructure.
Yes, Whiteswan seamlessly integrates with your current IT and security infrastructure, including endpoint protection, IAM, and PAM systems.
Whiteswan automates compliance with industry standards, offering continuous monitoring, detailed audit trails, and access controls to meet regulatory requirements.
Absolutely. Whiteswan enables secure remote access through identity-based Zero Trust controls, ensuring safe access to apps and infrastructure from anywhere.
Whiteswan offers tailored security solutions for every role, integrating identity and network protection to simplify operations and reduce complexity. Consolidate tools, automate compliance, and streamline access for employees and third parties with seamless Zero Trust deployment, while enforcing MFA and optimizing network performance for complete visibility and security.

Stay ahead of the curve and make the most of our platform with our expert advice and thought leadership.

Zero Standing Privileges (ZSP) is a leading cybersecurity practice that aims to prevent unauthorized users from gaining access or having their privileges escalated. “Ransomware attacks

Safeguard patient data with Whiteswan’s expert HIPAA compliance solutions. Discover how our identity security measures protect sensitive information. Learn more about HIPAA regulations and secure your organization’s future.

Key Takeaway:The discussion surrounding Zero Standing Privileges vs. Traditional Privileged Access Management (PAM) shows an important shift in cybersecurity strategy. Focusing on just-in-time access, decreasing